In the past, the site has published all types of sensitive top-secret information including US diplomatic cables and foreign exchange emails, emails from members of governing bodies for US political parties, espionage orders, and country negotiating positions on international trade agreements, among others.
On Tuesday, the latest bit of WikiLeaks content to be released was codenamed “Vault7” Year Zero and contains CIA internal documentation of a “massive arsenal” of some of the agency’s most important hacking tools used to penetrate systems around the world. Some of these techniques include weaponized “zero day” exploits, malware, viruses and remote control systems, to name a few. The website has carefully reviewed the zero-day exploits and has avoided distributing any “armed” cyberweapons until the worldwide security community can review how the information can be examined and disarmed before being released to the public.
While most third-party sources are unable to verify whether the Year Zero documents are real or have been altered, WikiLeaks founder Julian Assange said during a press conference streamed to Periscope, “We have quite a lot of exploits … that we want to disarm before we think about publishing it.”
Includes details on how to breach multiple desktop and mobile OSes
According to Assange, Vault 7 is the most comprehensive release of US spying files ever made public, with dates ranging over the past three years. The files include details on the software capabilities of the agency, such as how to compromise smart TVs, Apple iPhones, Android devices, and operating systems including Windows, Mac OS X, and Linux. Other copy-and-paste code included shows basic steps involved in the exploitation of a UEFI boot sequence. The first batched released so far contains 7,818 web pages with a total of 943 attachments from the Center for Cyber Intelligence.
Vault 7 "Weeping Angel" Smart TV exploit
“We’re going to work with some of these manufacturers to try and get these antidotes out there,” Assange says.
Of the leaks published so far, one of most alarming pieces of information include the suggestion that secure messaging apps using end-to-end encryption have been compromised as well. This would include the popular WhatsApp, Signal, Telegram, and even Confide – the one that White House staffers have been using to communicate outside of the CIA’s operational reach.
Security experts thus far, however, claim that the methods listed in the documents do not specify how to compromise the apps themselves but only the mobile operating systems they are used with. Snowden has also confirmed this via twitter, saying that iOS and Android platforms were compromised rather than individual communication apps using end-to-end encryption methods.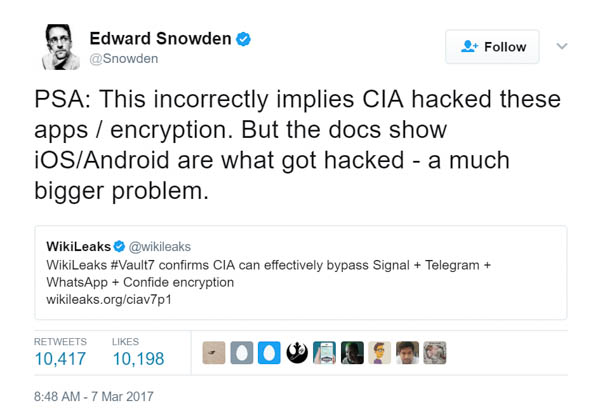
Assange: Android and iOS have “significant problems”
So far, Apple has said it patched most of the disclosed vulnerabilities with the latest release of iOS for its mobile users. Samsung, however, says it is “urgently looking” into the information after one of the documents listed a method to turn its Smart TV lineup into secret surveillance devices. Microsoft says it is aware of the alleged cyberweapon tools and it currently “looking into it.” Google says that it has already patched most vulnerabilities in the latest Android release but must inform its mobile partners that their custom releases of its software may still be left vulnerable.
Assange warns that due to the large variety of Android manufacturers, there is no way to automatically update each custom software install with the latest security patches. “That means that only people who are aware of it can fix it," Assange said. "Android is significantly more insecure than iOS, but both of them have significant problems."
According to Paul Rosenzweig, former deputy assistant secretary of policy at the US Department of Homeland Security, there is an “untold value” to the CIA if the tools are currently in use. He says it is unlikely that the CIA is the only group that knows about the holes, but there is “no reason” to think that some of these vulnerabilities have not already been disclosed to foreign governments including China and Russia.
“If Samsung TV is inside Vladimir Putin's home, this is a good thing [for the CIA].”
For now, the White House has yet to comment on the leaks, refusing to authenticate or confirm the existence of the tools. “I think obviously that's not something that has been fully evaluated,” said White House press secretary Sean Spicer. “And if it was, I would not comment from here on that.”

